Data Security Project
Roles During Project - UX Researcher
UX Methods Used - Surveys, User Interviews, Affinity Diagramming, Chi-Squared Statistical Testing
Tools Used - Atlas.ti, SPSS, Microsoft Office Suite
Purpose
The purpose of this project was to examine users' knowledge of safe cybersecurity practices and how they implement that knowledge when browsing online.
Processes Used
For this research study, we used a variety of user research methods to examine users' knowledge on practicing safe data security techniques while online. Below are the steps we used to complete this project.
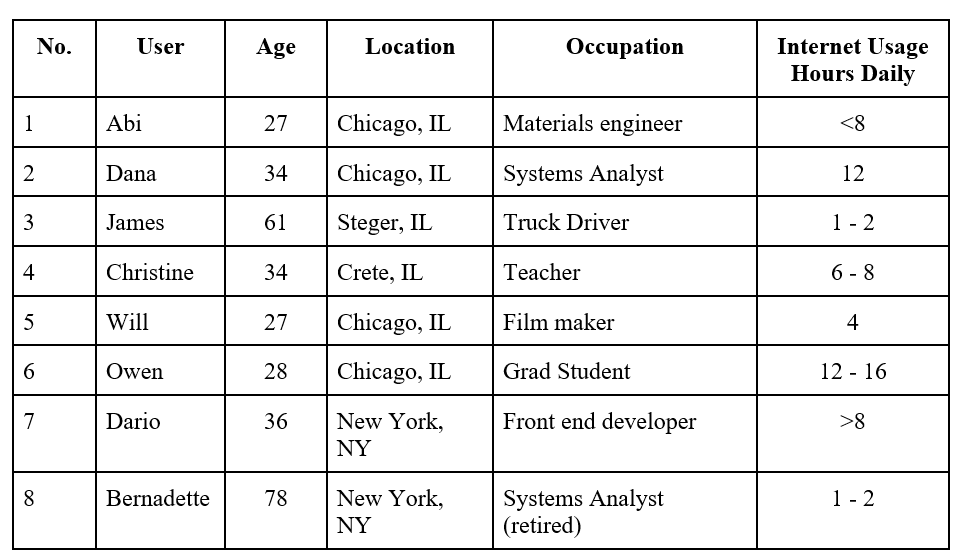
Step 1 - We observed how users interacted Google's Privacy Terms and Conditions by observing how they set up their Google Accounts. Below is a table that give us information on each participant.
Based on our observations, we set up an affinity diagram to identify the common patterns that occurred when users were performing these tasks.
Step 2 - We set up a user interview scripts to interview users on their knowledge of safe data security methods. After our user interviews, we used Atlas.ti to perform qualitative coding to determine common themes amongst the user interviews. Here's a link to the interview draft that we created: Interview Draft
Step 3 - After we performed qualitative coding on our user interviews, we created a survey using Qualtrics that consisted of 35 participants. The purpose of our survey was to gather users' knowledge and understanding of safe cybersecurity practices.
After the participants completed our survey, we performed a chi-squared analysis to analyze the categories of users who have knowledge of safe cybersecurity methods but don't practice them vs. users who don't have the knowledge or skillsets in practicing safe cybersecurity methods
Step 4 - Based on our chi-squared analysis, we worked on coming up with a solution for the proposed problem that was presented to us.
Results
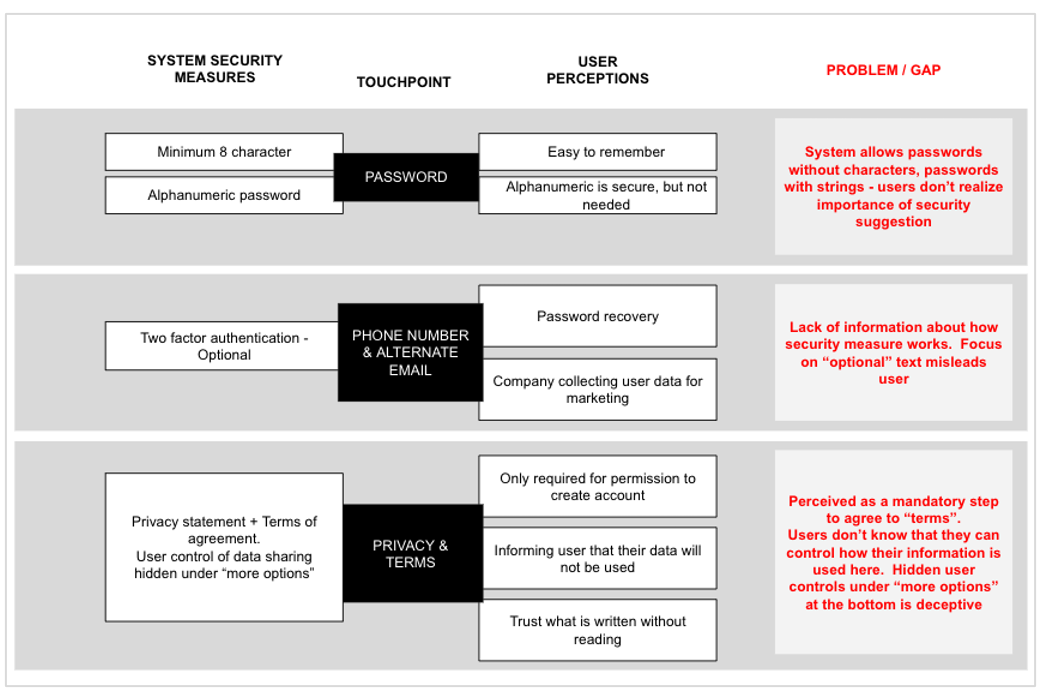
Results from Our Observations - During our
observations, we've noticed how users skipped the privacy terms
and agreement because of their preconceived notions to Google's Privacy Terms and Agreement. An
important
finding that
we've discovered in our affinity diagram
was how users prioritized password memorization over password security due to the number of
online
services and accounts that they use. Below is a visual of our affinity diagram that shows these
results.
Results from Our User Interviews and Survey - In our user interviews, we discovered that users trusted brand name websites for conducting payments and browser security. We also discovered that users saved their passwords on brand name web browsers because of their trust in them along with the convience these browsers gave users in password memorization. Below is a graph that represents the quantity of users that conduct credit card payments online.
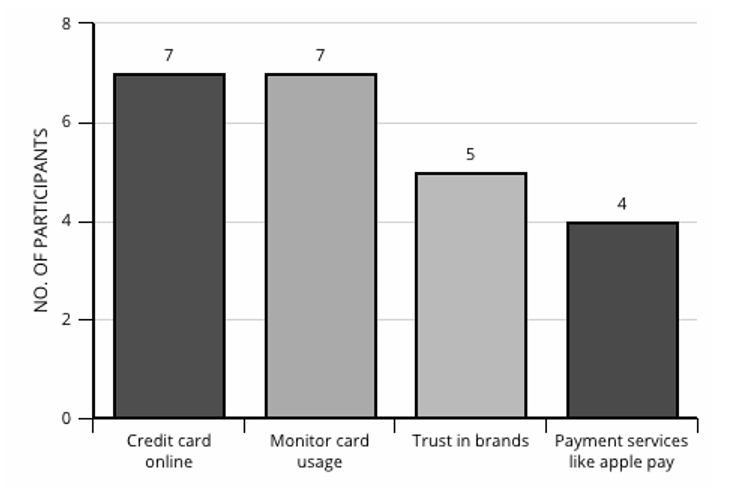
For our survey results, we conducted a chi-squared analysis and discovered that users trusted brand name websites than actually practicing safe cybersecurity methods.
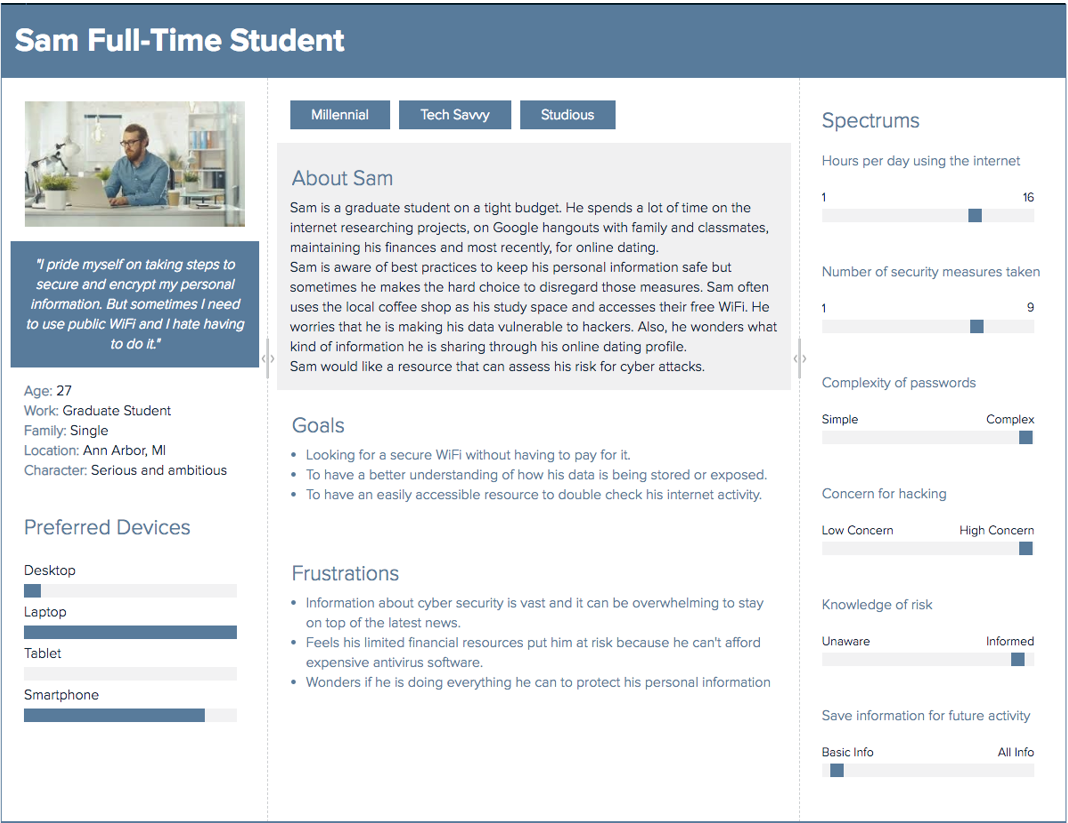
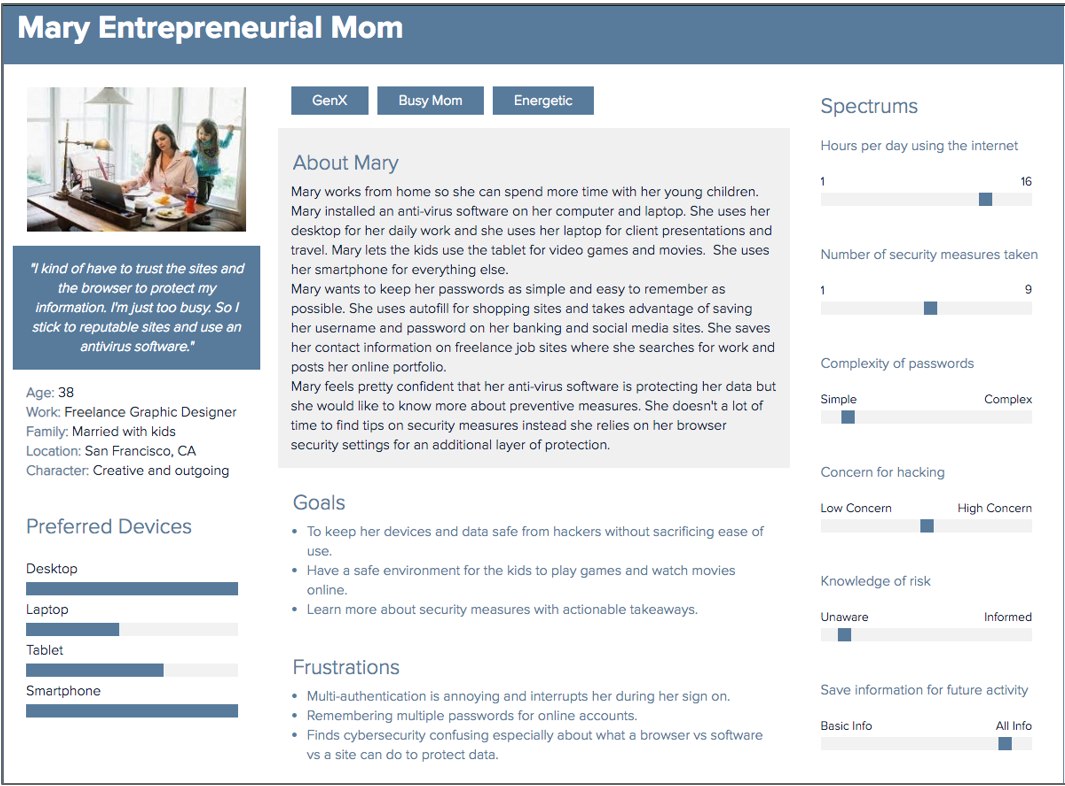
Personas and Feature Matrix - Based off of our survey, observations, and user interviews, it became clear to us that users did not have knowledge and/or the time to practice safe cybersecurity measures. To solve this issue, we decided to come up with a tool to help increase users' awareness of cybersecurity best practices when they're online. Here's a link to the feature matrix. Below are visuals of the personas that we created.